Cookies are used to remember your preferences and track your browsing activity across different websites. However, they can also pose a threat to your data privacy.
Category: Cybersecurity

Cybersecurity should play a role in every stage of the employee turnover process! There are security risks that can quickly blossom into a full-blown attack.

A ransomware group called Black Basta continues its reign of terror against organizations in the healthcare, manufacturing and technology sectors. The group has already claimed responsibility for several high-profile attacks, including an attack on a major US healthcare provider that resulted in the theft of patient data.

Users of X Blue will have to send more than just $8 a month for membership…they’re going to have to send photo verification along with ID, too.

We know that smart devices like your TV and refrigerator are more susceptible to cyberattacks than more advanced machines, like your work computer for example.
In response to this problem, the FCC is proposing a program that would label certain products as “strong enough” to meet the federal standards.

Not all applications are useful—or even safe. Thankfully, your IT team knows how to guarantee only secure apps end up installed on your system.

While private browsers make your online activities less visible to others who use the same computer, they don’t make you completely invisible.
Now Chrome users are seeking $5B in damages, alleging that the company excessively tracked activity while users in Incognito mode.
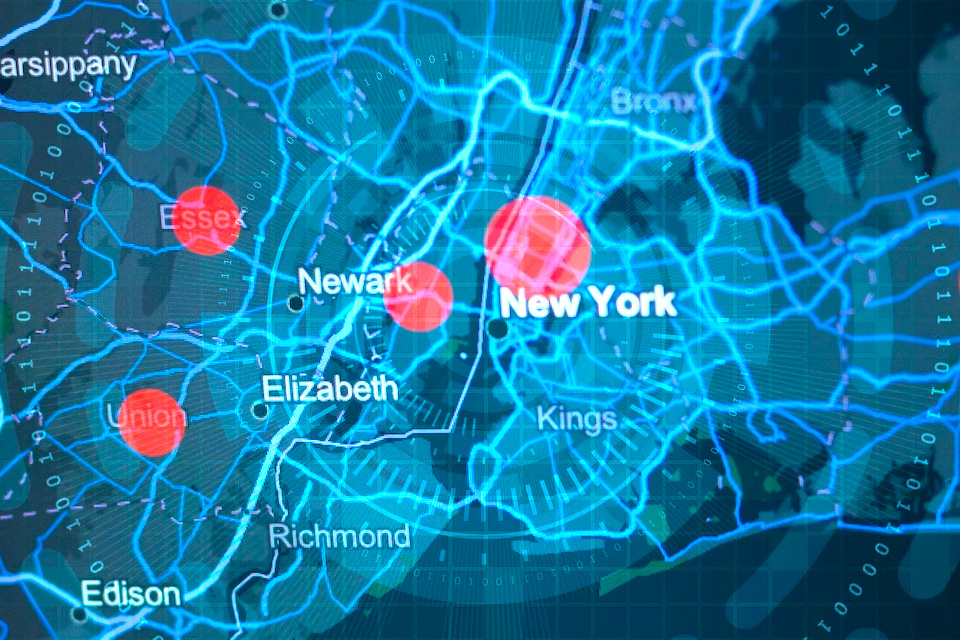
Maybe you’ve heard of geolocation, which knows exactly where you are on the map.
Geofencing takes that concept even further. It uses GPS, Wi-Fi, or cellular data to create a virtual boundary or perimeter around a physical location.

Whether you’re checking in to someplace on Facebook, or browsing posts made from a specific location on TikTok, you’ve probably come across geotags before—maybe you’ve even used a few!
It may shock you to hear this: Geotagging can pose cybersecurity and privacy risks if not properly managed!

How did this happen? It turns out even law enforcement are not immune to cybersecurity risks and data leaks.

