Honeypots are becoming increasingly important in today’s digital world, as they provide an additional layer of protection against cyber attacks. But what does the term really mean?
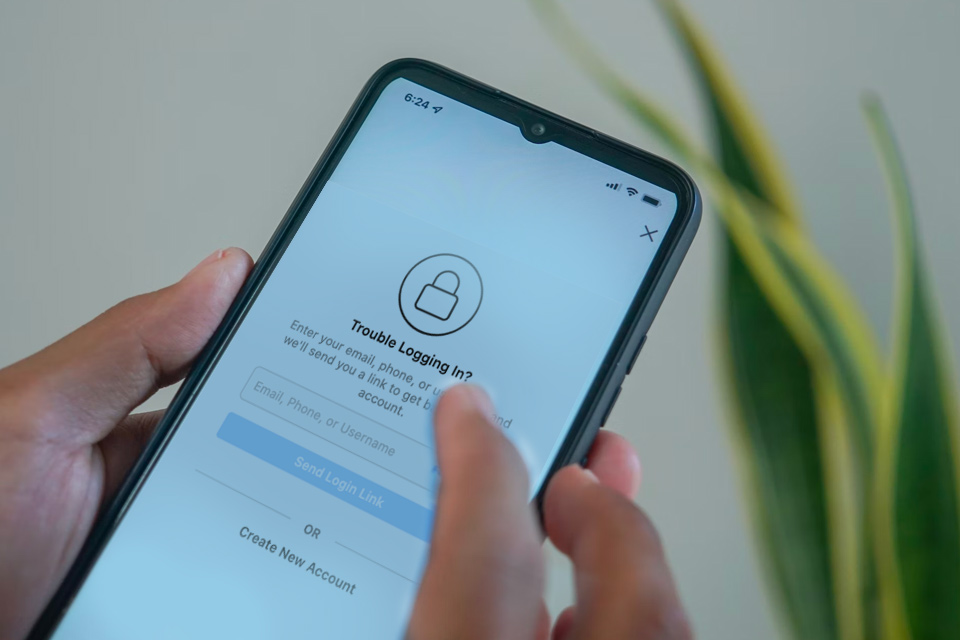
What happens if you don’t remember, or can no longer access, your MFA?
That’s where authentication recovery codes come in.

Recently, AT&T has been in the news due to a data breach that exposed sensitive customer information and caused potential financial losses. If you may have been one of the 9M customers affected, you’ll want to read on.

What’s behind this rise in mobile device theft, and what would such a crime mean for you?

What exactly is ChatGPT? What are its limitations and where does it excel? Should we be concerned about the progress its made in such short time? What does this all mean for the future of artificial intelligence and how we interact with it?
Read on to find all your answers.

A recent social engineering threat has emerged in the past few months. They play on emotions to get their target to react without thinking, in a way that allows the threat actor to gain access to your accounts or systems.
The problem is, it’s not you that they’re targeting this time.

What do you need to know about protecting your private data, in the event that YOUR telecom services are compromised?

Fresh out of the box, your phone probably had the provider’s preferred web browser; an application to Map your way around; somewhere to send messages and even backup data! What do you do with all these default programs?

In early February, a Reddit employee fell for a phishing scam. That led to a data breach exposed the administrators’ side of Reddit’s database.

Recently, an investigation into suspicious activity on GoDaddy servers uncovered a massive data breach that’s been ongoing since at least 2020.

