Here’s what you can do to protect your card information, whether you’re shopping in real life or online.
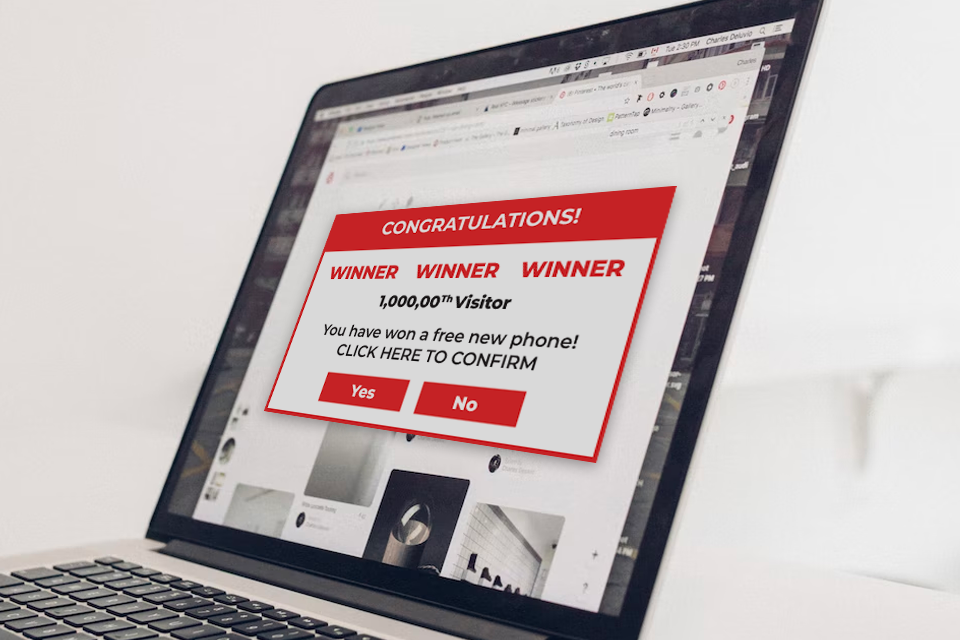
How can you keep yourself safe from this reverse social engineering tactic?

One of your most prized possessions shouldn’t be so vulnerable. Instead, take these 3 easy steps to better protect your iPhone data.

Brand new cyberattack strategies have come out of the woodwork. Have YOU been unintentionally putting private data at risk during video calls?

You may have heard about Business Email Compromise (BEC) scams before…Recently, cybercriminals have been engaging more and more often in what’s known as Business Identity Compromise.

Do convicts seem like an interesting choice for targets? In reality, their situation prevents them from reacting to the full extent necessary to contain threats.

Introduction If you used rideshare apps in 2016, then you’ll vividly remember the hack on Uber’s database that exposed 600K drivers’ license numbers and 57M

Threat actors can, and do, hack into webcams for nefarious purposes. Here’s what you can do to mitigate the threat of a hacker accessing the cameras on any of your devices.

The consequences of this data breach for customers could be severe, and throws into question the security of our data when we entrust so much personally identifying information (PII) to telecom companies.

American Airlines experienced a data breach recently…What happened to your data?

