As vaccination becomes more commonplace, bad actors are developing false proofs of vaccination to sell on the black market.

Although cyber liability insurance is meant to protect companies against such vicious losses, this coverage is often as clear as mud. So, let’s talk about the importance of cyber liability insurance and uncloud some common cyber terminology.
A new botnet called EwDoor has been recently discovered targeting AT&T devices based in the U.S.

A data breach could bottleneck your progress indefinitely or cause you to shutter. Here’s how to protect your growing company.

The tech sector will have to reckon with entirely new travel expectations, not just for right now, but for the foreseeable future too.

Monitoring and protecting your work accounts may not be enough to prevent a cyberattack. The tidbits gathered from your personal pages can be just as damaging.

As more cybersecurity jobs become available, ask yourself: Are we hiring the skills we actually need?

Phishing: It’s the last thing anyone wants to fall for and one of the most prevalent threats to businesses today.

Malware threats are evolving almost as fast as the cybersecurity designed to fight it. Here are the top five threatening businesses today.
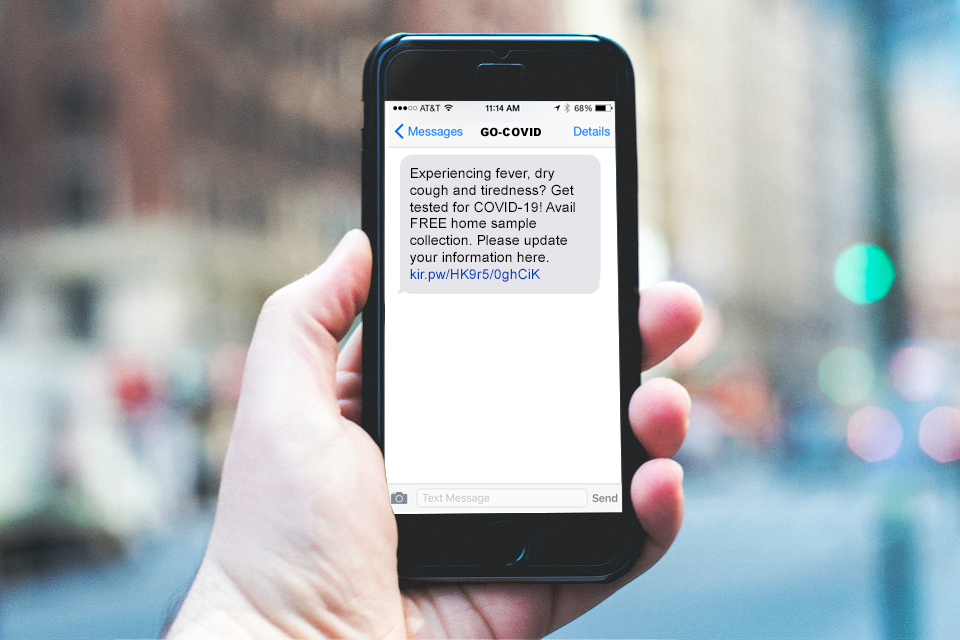
Smishing scams use text messages to gain trust.

